Helmut
November 17, 2023, 1:15pm
1
Hello,
I played around with the demo application of TMS Cryptography pack. What I have done:
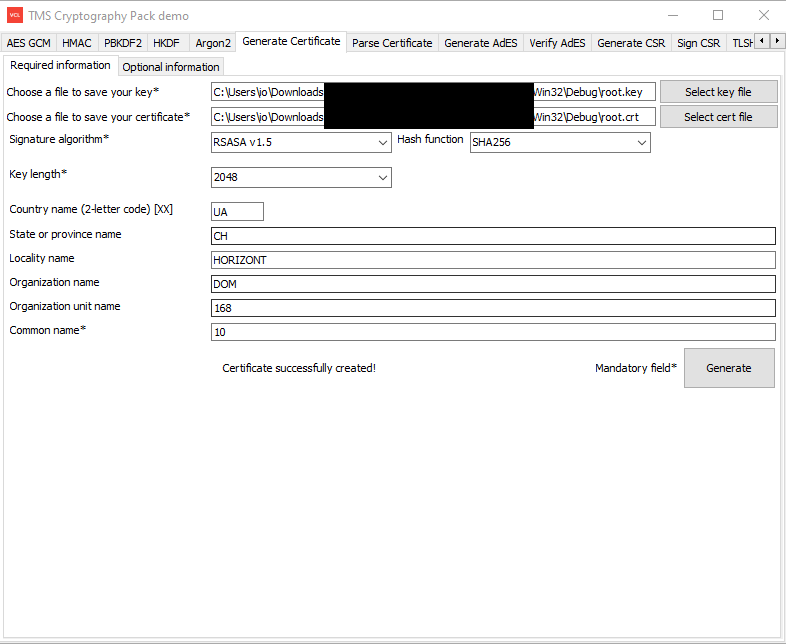
Created a CA certificate. In "optional information" I checked the option CA (see picture)
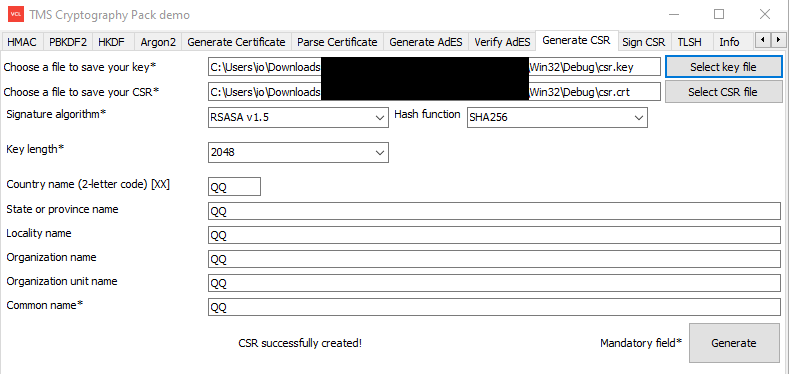
Created CSR:
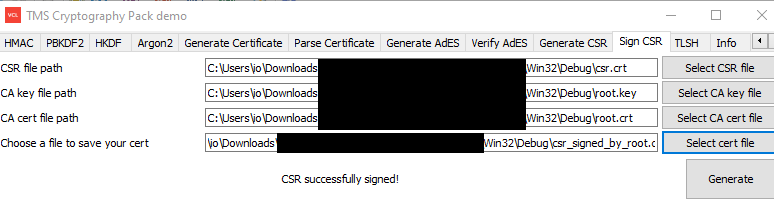
Signed the created CSR in 2. by the CA certificate in 1.
The result:
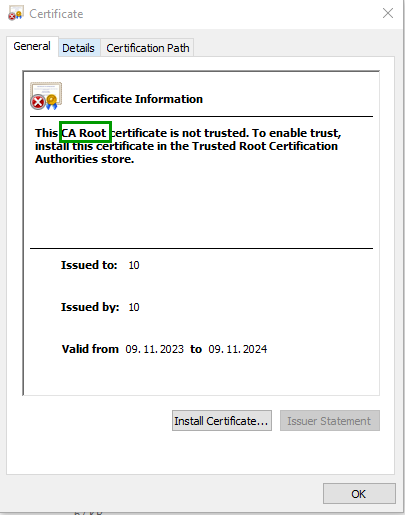
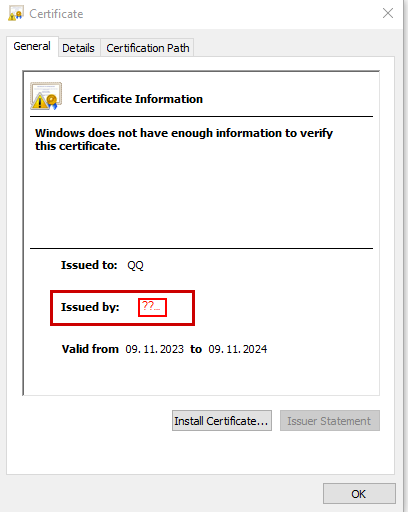
The opened CA looks like this:
The signed CSR looks like this. The issuer is missing, the signature is also missing.
When I am trying to open the signed CSR via ASN.1 Parser Online , it throws me an error:
Content size is not correct for container at offset 44
Via X509 Certificate Reader, Validation, Recovocation Checking and Conversion the signed CSR can not be opened neither.
My questions are:
How to add the issuer to the signed CSR?
How to add the signature?
Why the signed CSR can not be opened by the online tools you have provided? Is that a bug?
And in general, is the signing process correct?
Thank you for your effort and help!
Helmut
November 17, 2023, 1:45pm
2
@wlandgraf Could you please move this ticket also to TMS Cryptography?
p.s. Currently I am evaluating the crypto pack trial version and face some issues. Why is it not possible to create topics directly in the TMS Cryptography category!?
Thanks for your help!
wlandgraf
November 17, 2023, 2:00pm
3
Because you are not a registered user.
Bernard
November 19, 2023, 1:27pm
4
That's because it is a self signed CSR.
To add the 'issuer' and 'issuer signature' requires the modification of the crt_request_RSA (and ECDSA) functions.
On question 3, I don't know, your example CSRs open well in all tools I have tested. There may be an issue with CRLF handling with some tools.
Helmut
November 21, 2023, 7:17pm
5
That's because it is a self signed CSR.
As far as I know, there is no such thing like "a self signed CSR". What exactly do you mean with "a self signed CSR"!?
To add the 'issuer' and 'issuer signature' requires the modification of the crt_request_RSA (and ECDSA) functions
Would you please provide this functionality?
On question 3, I don't know, your example CSRs open well in all tools I have tested. There may be an issue with CRLF handling with some tools.
Please try the following:
Generate via TX509CSR a new CSR
Sign it via TX509Certificate.SignCsr
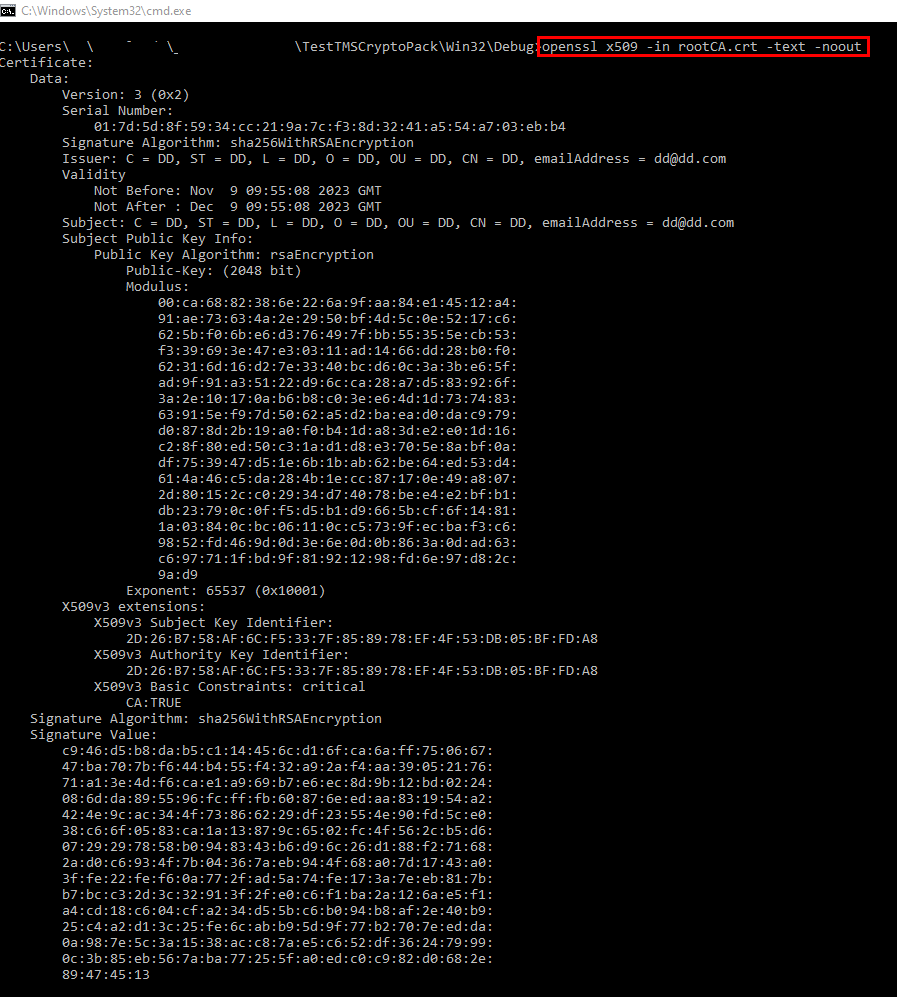
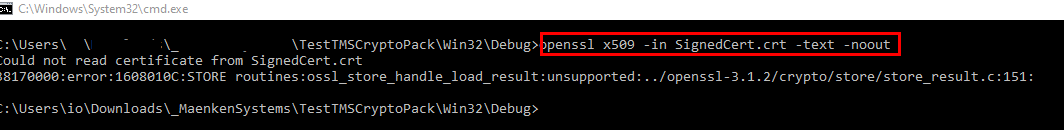
Try to view the signed cert via openssl
Here is the code:
procedure TForm3.Button1Click(Sender: TObject);
begin
X509CSR1.KeyFilePath := 'entity.key';
X509CSR1.CSRFilePath := 'entity.csr';
X509CSR1.signatureAlgorithm := TSignAlgo.sa_sha256rsa;
X509CSR1.hashFunction := TX509HashFunction.sha256;
X509CSR1.BitSizeEncryptionAlgorithm := 2048;
X509CSR1.countryName := 'DE';
X509CSR1.stateName := 'Berlin';
X509CSR1.OrganizationName := 'Name';
X509CSR1.OrganizationUnitName := 'Unit';
X509CSR1.commonName := 'SomeValue';
X509CSR1.SetVersion('1');
X509CSR1.Generate;
end;
procedure TForm3.Button3Click(Sender: TObject);
begin
X509Certificate1.KeyFilePath := 'rootCA.key';
X509Certificate1.CrtFilePath := 'rootCA.crt';
X509Certificate1.SignCSR(X509CSR1.CSRFilePath, 'SignedCert.crt');
end;
Here are the openssl outputs:
Bernard
November 22, 2023, 4:37pm
6
Noted. There is a bug in the version assignment and parsing and the current CSR has the same input for owner and issuer.
1 Like