Suppose I have an XData server and I want three levels of access rights to the API. Let's say User, PowerUser and Admin I can then control access through the EntityAuthorizeScopes attribute. For example:
[Entity, Automapping]
[EntityAuthorizeScopes('User', EntitySetPermissionsRead)]
[EntityAuthorizeScopes('PowerUser', EntitySetPermissionsWrite)]
TMyEntityClass = class
The XData server can access the database with a single (DB server) user account.
In the SphinxConfig.OnConfigureToken event, I suppose I can add the claim(s) to pass the user level(s) to the XData server.
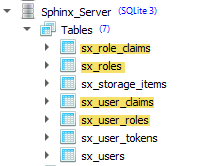
Looking at the database generated by Sphinx, I see various tables that seem to associate users with roles and claims (all empty by default):
- Is there any documentation on these tables (or associated entities: TUsers, TUserRoles, etc.) and how these work together (e.g. a data model)? I have looked everywhere but I cannot seem to find anything.
- Are these entities (tables) indeed meant to be used for scenarios as described above or are they reserved for other purposes?
- Must I 'manually' add the claim (e.g. 'PowerUser') to the token in the SphinxConfig.OnConfigToken event or is this done automatically by Sphinx if these tables (entities) are populated? Tables like sx_role_claims and sx_user_claims seem to suggest something to that extent...
Thanks for clarifying!